Modern warfare has become a deadly game of hide and seek. In recent decades, precision-guided weapons and advanced reconnaissance technologies have created a new rule on the battlefield: if you can be located you can be destroyed. Stealth technology emerged to cope with this new reality, offering a means of concealment from radar and other sensors, and thus an increased chance of survival, for combat aircraft, ships, and ground forces. I will explain the origins, workings, and prospects for military stealth technology and reveal some inconvenient truths about its utility.
The earliest methods of stealth in warfare were intended to avoid visual detection. Camouflage, tunneling, and nighttime maneuvers were often effective in conferring a battlefield advantage. Today radar, infrared, and acoustic detection technologies make concealment of military movement difficult, day or night. Enter stealth technology, which was introduced as a primary design element by the radar-evading U.S. F-117 attack fighter in 1983. Subsequent USAF combat aircraft, including the B-2 bomber and the F-22 and F-35 fighters, have incorporated progressively more refined stealth techniques. The stealth concept has also been applied to naval combatants and even to some army vehicles.
F117 Nighthawk stealthy tactical bomber
Aircraft Stealth
There are three design methods aircraft engineers have used to reduce the operational visibility of warplanes: geometry, coatings, and heat suppression. By carefully designing the shape of an aircraft to minimize radar reflections, the effectiveness of radar tracking can be reduced considerably. Coating the skin of the plane with radar-absorbing material (RAM) further reduces the radar “signature,” and suppressing the emission of heat from the plane’s engines, lowers the visibility of the aircraft in the infrared spectrum. Even the missiles launched from stealthy aircraft have been designed to be stealthy, further adding to the potency of these weapons. All these measures increase the cost of an aircraft, both initially and for maintenance over its operational life.
Naval Stealth
The introduction of submarine warfare was the first, and arguably most effective, implementation of stealth in naval warfare. Missile submarines are the backbone of the U.S. strategic nuclear deterrent, and attack submarines are the deadliest threat to surface ships. Radar is not a threat to submerged submarines, but sonar is used to detect them. Thus, great efforts have been made to reduce the acoustic signatures of subs, making them as quiet as possible. Surface ships have been redesigned to apply the methods of radar signature reduction developed for stealthy aircraft. The newest surface combatants look quite different from their predecessors, with smooth, uncluttered surfaces covered by radar-absorbing coatings. While these methods cannot be applied to U.S. aircraft carriers, many of the aircraft that fly from them are naval versions of the stealthy F-35.

USS Zumwalt – Stealth at sea
Army Stealth
While the stealth technology implementation efforts of the U.S. Army are not as advanced as those of the other services, efforts are under way to reduce the vulnerability of Army vehicles and personnel. Newer Army attack helicopters incorporate some stealth features, and the latest developments in vehicle and soldier camouflage include measures to reduce the thermal signature of ground forces.
The Limits of Stealth
Stealth technology is a genuine advance in the art of weaponry, but it is not a guarantee of military dominance. The history of warfare is one of measures and countermeasures, and stealth technology is no exception. The following issues will limit the impact of stealth on warfare.
Competition
Although the U.S. took an early lead in developing stealthy aircraft, fielding two fighters (F-22 and F-35) and two bombers (F-117 and B1) between 1981 and 2006, The other superpowers followed suit: Russia with the SU-57 fighter in 2010 and China with the J-20 fighter in 2011 and the J-35 in 2021. Production of the U.S. B-21 has just begun, but the newly announced U.S. F-47 fighter is only in early development, while China’s new J-36 and J-50 prototypes have already been sighted in the air. Technical details of all of these planes are classified, but it is clear that the U.S. no longer enjoys a monopoly in stealth aircraft
Cost
Stealth is expensive. The following table show the comparative costs of U.S. stealth aircraft compared to their non-stealthy equivalents. Note that the cost differential is not limited to the initial procurement. The maintenance costs are also higher because of their greater complexity and the need to maintain the stealth coatings of the aircraft.
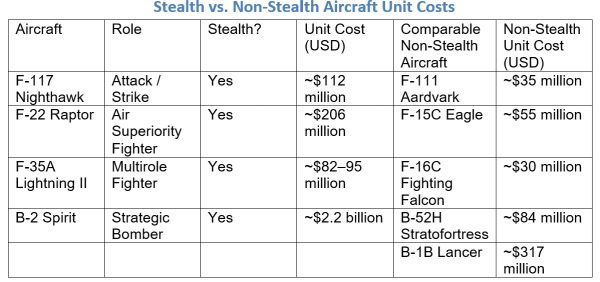
The cost factor is the reason why it would be infeasible to redesign military transport, refueling, and surveillance aircraft to make them stealthy.
Detection Advances
As the U.S. deployed stealthy warplanes, other major nations developed and fielded improved radar systems, such as the Russian Nebo-M, Voronezh, and P-18, which use VLF and UHF frequencies that can detect stealthy aircraft. Even regional powers, like Iran, have deployed new radars with improved detection capabilities to counter stealth aircraft. Another counter-stealth method is networking radars to locate such aircraft by scanning from multiple directions. Early research on photonic radar, which relies on laser light rather than radio frequency waves, indicates a promising potential to detect and track stealthy aircraft.

Iranian Ghadir anti-stealth radar
Logistical Vulnerability
While stealthy planes may be less vulnerable in the air, they are highly vulnerable on the ground, and they are reliant on the planes, ships, and bases that supply them with fuel and weapons. Of particular concern are the tanker aircraft that are essential to long-distance air power projection. The Air Force currently operates approximately 600 aerial refueling planes, and none of them are stealthy. Their destruction would cripple the ability of stealthy aircraft to conduct long-range campaigns. U.S. transport and airborne radar aircraft also lack stealth characteristics, and thus would be easy prey in a future war. Finally, the air bases from which stealthy aircraft operate cannot be concealed, and they would be high priority targets for missile attack.

KC135 aerial refueling tanker – zero stealth
The Future of Stealth
The simplest way to overcome the cost and detection problems limiting the efficacy of stealth technology is to reduce the size of weapons. The crucial metric of stealth in the radar spectrum is the Radar Cross Section (RCS), and this is roughly proportional to the size of the aircraft/vessel/vehicle. Similarly, visual and infrared signatures diminish with size. Thus, the easiest and cheapest way to achieve improved stealth is to replace manned weapons with smaller and cheaper robotic systems. Providing superior stealth characteristics at lower cost, is yet another factor which will drive the displacement of manned aircraft, ships, and ground vehicles by their drone equivalents. However, perverse vendor incentives and military institutional inertia will likely lead to further costly and troubled manned stealth aircraft programs, such as the B-21 bomber and the newly-announced F-47 development project.

Depiction of U.S. F-47 sixth generation stealth fighter
Conclusion
Stealth technology, while functionally appealing to the military, is a classic example of arms racing, in which new developments spur competitive and counteractive efforts in other nations. Stealth is unlikely to be decisive in future wars because it is irrelevant in asymmetric conflicts, such as the current U.S. campaign against the Houthis in Yemen, and it will likely face comparably protected planes, ships, and troops in a war with a peer adversary. In a large-scale conflict, stealth may protect some planes and ships, but it cannot shield the vulnerable bases and logistical units that are essential to successful military operations.

Andersen Air Force Base, Guam – Prime target?
Military considerations aside, it may be said that the greatest triumph of stealth was in the domain of U.S. defense politics. At the start of the F-35 program, clever lobbying by contractors and the Pentagon reduced the acceptance testing rigor for this vast undertaking. This allowed the troubled project to figuratively fly under the radar of effective oversight. When the Defense department committed to low-rate production of the F-35 before the completion of normal testing in 2001, the result was building many aircraft that would later require costly upgrades. The F-35 has still not met all its testing requirements. Undeterred by the problems of the F-35, in the 2016 National Defense Authorization Act, Congress established the Middle Tier Acquisition pathway (MTA), which substantially reduced testing requirements for high-priority weapons projects. Thus, whatever the outcome of future armed conflicts, stealth in weapons engineering and in lobbying tactics will continue to bring growing income to arms makers, the biggest winners in arms racing.